Intro
I chose to do this write-up on LazySysAdmin because it is a good box for potential OSCP students to start out on and something that every OSCP pentester and every current OSCP (PWK) student that is ready to take the exam should be able to do without using a walk-through. This box should take 6 hours or less if you do not experience any hang ups or interruptions.
NMAP Enumeration
My first initial NMAP scan I did a service scan on all 65535 ports. I usually port scan in two steps; First finding all ports that are open and then running a service scan against only the open ports in order to save time during the reconnaissance phase.

Nmap Service Scan against all ports

Nmap Scan Results
Web Enumeration
To start my web enumeration I began with a basic Nikto scan of the target machine. In doing so reveals several notable webpages to investigate further.

Basic Nikto Web Scan
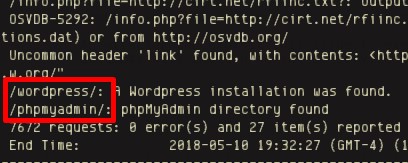
Scan Detected 2 Notable Webpages
We will note these pages for further enumeration.
WPSCAN
Having discovered that a possible WordPress site was running on the target machine, wpscan was used immediately after the web-scan completed. The user Admin was discovered.

Command used to enumerate wordpress users

User enumerated using the “–enumerate u” flag
SMB Enumeration
To begin SMB enumeration, enum4linux was used for the initial scan. The scan results revealed several shares that could be connected to using the smbclient. Using information that was gathered from the initial SMB enumeration via enum4linx along with the username discovered during the wpscan, allowed for a precise SMB connection using the smbclient, to be made.
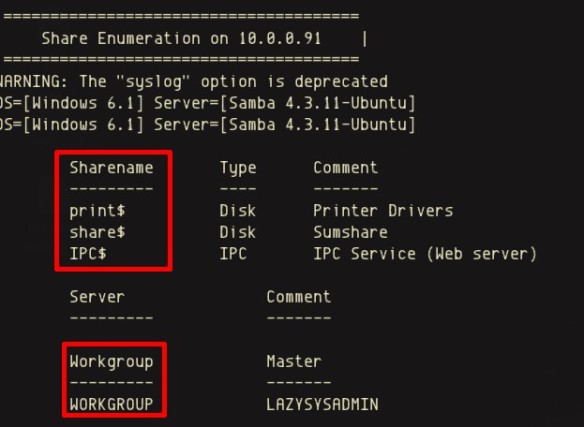
Enum4linux Share Details

Connecting to the interactive share via the smbclient
Having connected to the SMB share named share$, allowed for the wp-config file and several other files containing passwords to be retrieved.
The /wordpress/wp-config file revealed to following username and password combination:
Admin
TogieMYSQL12345^^
The deets.txt file revealed to following password:
12345
